
CYBER SECURITY
We provide a complete one-stop service for all cyber security solutions, including the proofing of systems against quantum computers.
Contact us at neom@samarium.group for a first free assessment.
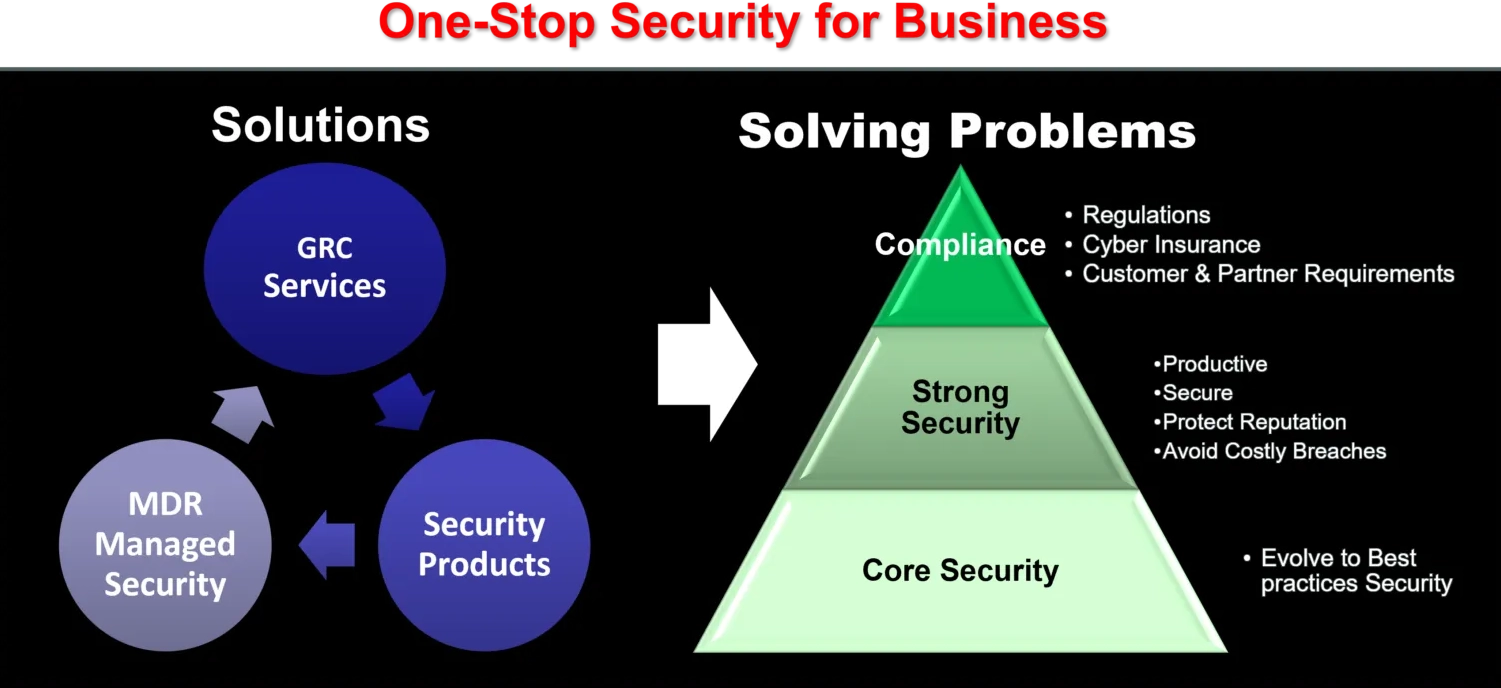
Integrated + Complete Cyber Security Solutions for Businesses and the Defence Industry
We design and implement transformational enterprise security programs, organizational constructs, and capabilities, so you can better manage cyber risks aligned with business priorities.
Capabilities include:
- Cyber assessments, frameworks, and benchmarking
- Cyber strategy and program transformation
- Cyber metrics, reporting, and risk quantification
- Cyber awareness, board reporting, and training
- Integrated risk management/governance, risk management, and compliance
- Third-party cyber risk
- Insider threat programs
Tactical Incidence Management: Detection – Response, Action, Prevention
Our team offers services to proactively monitor, detect, and respond to the toughest cyber threats, providing expertise without having to hire and manage yourself. We offer you the services and operations of a private security contract in the cyber and internet space. Decisive counteraction and robust response will deter any future criminal actors and attackers.
Capabilities include:
- Cyber incident hunting, detection, and response
- Managed and hybrid operate security services
- Advising and implementing solutions
- Cyber threat intelligence and analytics
- Security operations development
1. Security Architecture & Secure System Design
We design security architectures that are integrated into the system lifecycle rather than layered on after deployment.
Capabilities
Zero Trust architecture design
Network segmentation and micro-segmentation
Secure cloud and hybrid architectures
Identity and access management (IAM) models
Privileged access management (PAM)
Secure API and service-to-service communication
Defense-in-depth strategies
Advantage
Security decisions are made at the architecture level, reducing attack surface, operational complexity, and future remediation costs.
2. Threat Modeling & Risk Analysis
We apply structured threat modeling to identify and prioritize realistic attack paths.
Methodology
STRIDE, attack trees, and adversary modeling
MITRE ATT&CK mapping for attacker techniques
Business impact analysis (BIA)
Risk quantification and prioritization
Supply chain and third-party risk assessment
Advantage
Clients receive actionable, prioritized risk intelligence, not generic risk lists. Security investments are aligned with real threats and business impact.
3. Penetration Testing & Red Teaming
We perform offensive security testing to validate defenses under real-world conditions.
Services
Network penetration testing (internal & external)
Web, API, and mobile application testing
Cloud security testing
Active Directory and identity compromise scenarios
Red team operations and adversary emulation
Physical and social engineering (where authorized)
Reporting
Clear attack paths and root-cause analysis
Reproducible technical findings
Risk-based severity classification
Concrete remediation guidance
Advantage
Our testing goes beyond vulnerability scanning and focuses on what an attacker can actually achieve.
4. Secure Software & Application Security
We help organizations build and maintain secure software systems.
Capabilities
Secure software development lifecycle (SSDLC) design
Code reviews and architecture reviews
Static and dynamic application security testing (SAST/DAST)
Dependency and supply-chain security analysis
Secure CI/CD pipeline design
Hardening of runtime environments
Advantage
Security is embedded into development workflows, enabling faster releases without increased risk.
5. Incident Response & Digital Forensics
We support organizations before, during, and after security incidents.
Services
Incident response planning and playbooks
Breach containment and eradication
Digital forensics and evidence preservation
Malware and intrusion analysis
Post-incident root cause analysis
Regulatory and legal support preparation
Advantage
Clients gain technical clarity and control during crises, minimizing downtime, data loss, and reputational damage.
6. Security Monitoring & Detection Engineering
We design detection capabilities that identify real threats rather than generate noise.
Capabilities
SIEM and SOC architecture design
Log pipeline engineering
Detection engineering mapped to MITRE ATT&CK
Use-case development and tuning
Threat hunting frameworks
Integration of EDR/XDR platforms
Advantage
Detection focuses on attacker behavior, not just alerts, improving response time and reducing false positives.
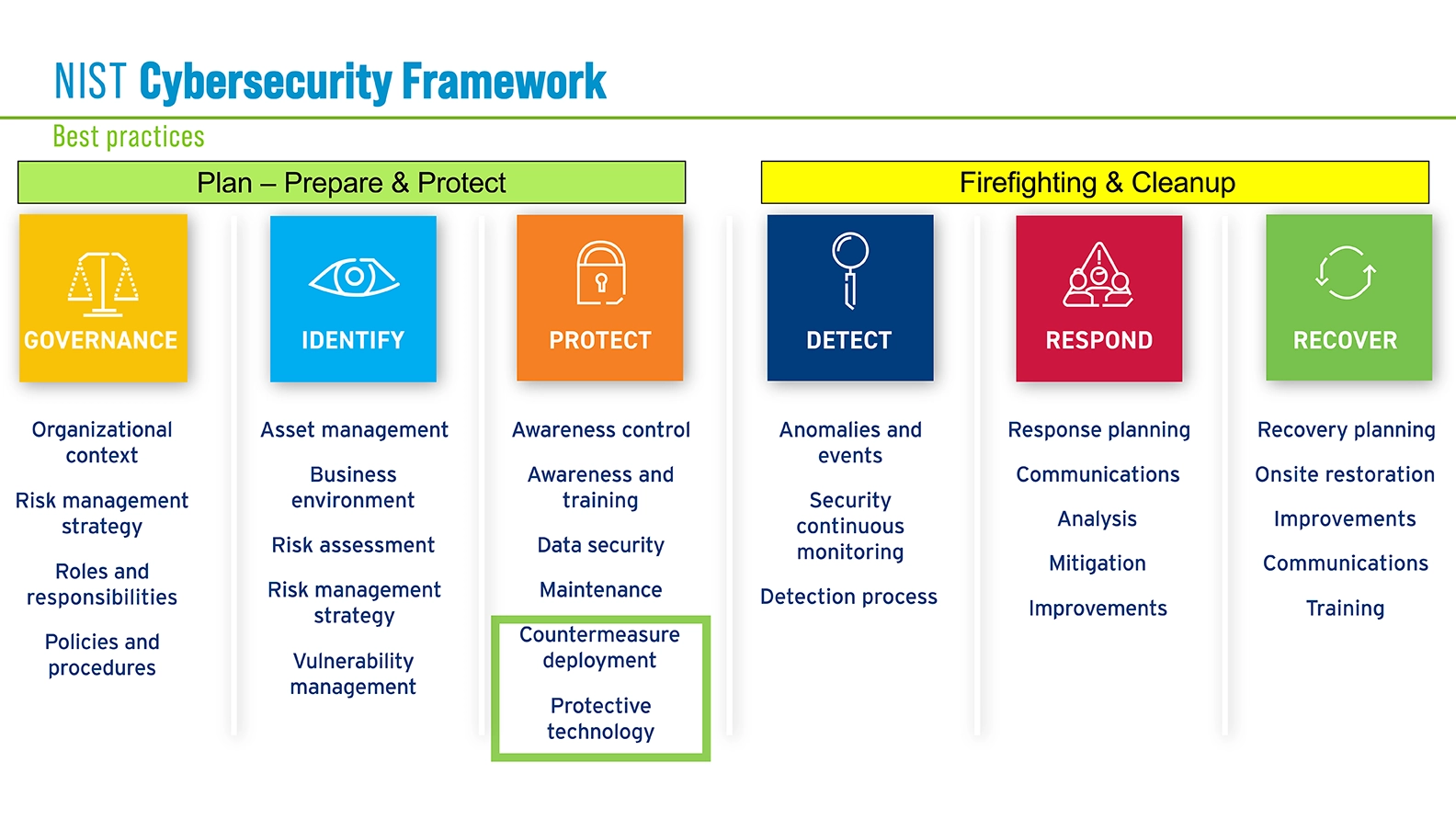
7. Governance, Compliance & Security Strategy
We help translate technical security into governance and executive-level clarity.
Frameworks & Standards
ISO/IEC 27001 & 27002
NIST Cybersecurity Framework
NIST SP 800-53 / 800-61
CIS Critical Security Controls
Industry-specific regulatory requirements
Advantage
Compliance is treated as a by-product of strong security, not as the primary goal.
Why Hire Samarium Group Corporation
1. Engineering-First Security
Our teams consist of security engineers and architects, not checkbox auditors. Every recommendation is technically grounded and implementable.
2. Security by Design, Not Afterthought
We integrate security into architecture, development, and operations—reducing long-term risk and cost.
3. Real-World Threat Focus
Our methodologies are aligned with how attackers actually operate, not theoretical models.
4. Vendor-Neutral Approach
We recommend tools and platforms based on technical suitability, not partnerships or commissions.
5. Clear, Actionable Deliverables
Clients receive documentation and guidance that engineers, security teams, and executives can all act on.
6. Trusted Partner for Critical Environments
We are experienced in environments where availability, integrity, and confidentiality are mission-critical.
Contact us at neom@samarium.group for a first free assessment.
